In a dramatic turn of events, crypto exchange Kraken has announced the recovery of $3 million from CertiK, the blockchain security firm that exploited a vulnerability in its system. What started as a supposed whitehat operation quickly spiraled into a public dispute, raising questions about ethical boundaries in cybersecurity and the responsibilities of security researchers.
Kraken Gets Its Money Back: A Timeline of Events
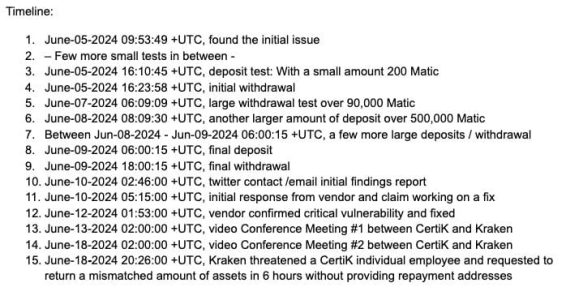
The saga began when CertiK identified a bug in Kraken’s system that allowed for the artificial inflation of balances. Instead of simply reporting the vulnerability, CertiK drained $3 million from Kraken’s treasury as a “demonstration.” This move ignited controversy, with many questioning CertiK’s motives and methods.
Here’s a quick timeline of the key events:
- January: Vulnerability exists, allowing balance inflation.
- June: CertiK identifies and exploits the vulnerability, withdrawing $3 million.
- Following days: Kraken patches the bug.
- Days later: Public dispute ensues over the return of funds and ethical considerations.
- Later: Funds are returned to Kraken (minus fees).
Whitehat or Blackhat? The Controversy Unfolds
The core of the controversy lies in whether CertiK’s actions qualify as a legitimate whitehat operation. Whitehat hackers typically disclose vulnerabilities responsibly and work with companies to fix them, often receiving a bounty for their efforts. However, CertiK’s approach deviated significantly from this norm.
Here’s why Kraken and the wider crypto community raised concerns:
- Bounty Protocol: CertiK did not follow Kraken’s established whitehat bounty program procedures.
- Excessive Withdrawal: The amount withdrawn ($3 million) was deemed excessive for a simple demonstration of the vulnerability.
- Delayed Return: CertiK initially refused to return the funds until Kraken provided an estimate of potential losses.
CertiK’s Perspective: A Necessary Test?
CertiK defended its actions by arguing that the large withdrawal was necessary to test the limits of Kraken’s security alerts and risk controls. According to CertiK, the fact that millions could be drained without triggering alarms highlighted the severity of the vulnerability.
CertiK also stated that they never requested a bounty and were focused on ensuring the issue was resolved. They contested Kraken’s claims of threats and demanded repayment in a different crypto amount.
A key point from CertiK’s perspective:
“We never mentioned any bounty request. It was Kraken which first mentioned their bounty to us, while we responded that the bounty was not the priority topic and we wanted to make sure the issue was fixed.”
Money Returned, but Questions Remain
Ultimately, Kraken confirmed the return of the funds (minus fees). However, the incident has left a lingering debate about the ethics of vulnerability disclosure and the responsibilities of security researchers.
Key questions that remain:
- What constitutes ethical behavior when uncovering security vulnerabilities?
- How much is too much when demonstrating a vulnerability’s impact?
- Should security researchers be entitled to compensation even if they don’t follow established bounty programs?
The Takeaway: A Need for Clear Guidelines
The Kraken-CertiK saga underscores the need for clearer guidelines and ethical standards within the cybersecurity community. While whitehat hacking plays a crucial role in identifying and mitigating vulnerabilities, it’s essential to ensure that such activities are conducted responsibly and ethically. This incident serves as a reminder that the line between whitehat and blackhat can be blurry, and a strong ethical compass is crucial for navigating the complex landscape of cybersecurity.
Disclaimer: The information provided is not trading advice, Bitcoinworld.co.in holds no liability for any investments made based on the information provided on this page. We strongly recommend independent research and/or consultation with a qualified professional before making any investment decisions.



