In a dramatic turn of events in the crypto world, leading exchange Kraken has successfully recovered nearly $3 million in digital assets. The funds were initially withdrawn by blockchain security firm CertiK, following what began as a white-hat hack. But this isn’t your typical story of bug bounty success. Allegations of extortion quickly surfaced, casting a shadow over the entire incident. Let’s dive into the details of this unfolding saga and understand what really happened between Kraken and CertiK.
The $3 Million Crypto Puzzle: How Did It All Start?
On June 20th, Kraken’s Chief Security Officer, Nick Percoco, announced on X (formerly Twitter) the recovery of the substantial sum. This confirmation came after a period of intense speculation and controversy sparked by Kraken’s initial claims of a ‘security researcher’ maliciously withdrawing funds. Percoco’s tweet signaled a resolution, stating the funds were back, minus transaction fees.
Funds have been returned. https://t.co/ejv4m0YxgE
— Nick Percoco (@c7five) June 20, 2024
Just a day prior, on June 19th, Percoco had publicly revealed the missing $3 million, pointing fingers at a “security researcher” for exploiting a bug and then refusing to return the assets without demands. Kraken’s accusations painted a picture of extortion, claiming the researcher wanted a reward and a meeting with their business development team before returning the crypto.
CertiK Steps into the Spotlight: From Researcher to ‘Accused’
Responding to Kraken’s accusations, CertiK, a well-known name in blockchain security, publicly identified themselves as the “security researcher” in question. They aimed to set the record straight and counter the narrative of malicious intent. CertiK’s move was a bold attempt to manage the escalating public relations crisis and present their version of events.
CertiK, in their own X post on June 19th, stated they had indeed informed Kraken about a vulnerability that allowed the withdrawal of millions. However, they flipped the script, alleging that *they* were the ones being threatened by Kraken’s security team.
“After initial successful conversions on identifying and fixing the vulnerability, Kraken’s security operation team has THREATENED individual CertiK employees to repay a MISMATCHED amount of crypto in an UNREASONABLE time even WITHOUT providing repayment addresses,” CertiK claimed, highlighting a starkly different experience from Kraken’s portrayal.
To further support their claims and provide transparency, CertiK released a detailed timeline of events. This timeline aimed to illustrate the entire communication process, starting from their discovery of the exploit on June 5th.
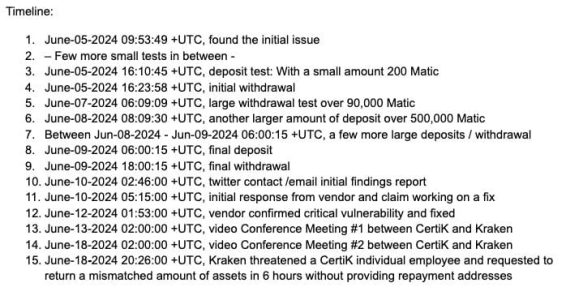
The Million-Dollar Question: Why Withdraw $3M Instead of $4?
Kraken’s CSO pointed out that an initial, small transaction of just $4 would have been sufficient to demonstrate the bug and qualify for a bounty reward. This raised eyebrows – why did CertiK withdraw such a massive amount, nearly $3 million?
CertiK’s explanation came in a subsequent X post after the funds were returned. They addressed the core question head-on, justifying the large withdrawal as a necessary step to thoroughly test Kraken’s security measures.
“We want to test the limit of Kraken’s protection and risk controls,” CertiK stated. “After multiple tests across multiple days and close to $3 million worth of crypto, no alerts were triggered and we still haven’t figured out the limit.”
Regarding the Kraken Security Incident
To address community questions and clarify the situation, we want to provide further details:
1. No bounty request was ever mentioned by CertiK to Kraken. It was Kraken who first mentioned their bounty to us. We responded that bounty is not the priority topic… https://t.co/EjQ5s8kEnS
— CertiK Security Leaderboard (@CertiK) June 19, 2024
Furthermore, CertiK disputed Kraken’s claim about extortion related to a bounty. They emphasized that they never asked for a bounty and that it was Kraken who first brought it up. CertiK maintained their focus was solely on ensuring the vulnerability was fixed, not on financial gain through a bounty program.
Adding another layer to their defense, CertiK highlighted that the funds were “minted out of air,” meaning no Kraken users were financially impacted by their actions. This was a crucial point in mitigating potential public backlash and reinforcing their white-hat hacker image.
Ethical Hacking in the Spotlight: Where’s the Line?
The Kraken-CertiK incident has ignited a significant debate within the crypto and cybersecurity communities. Key questions are being raised about:
- Ethical Boundaries: Where is the line between legitimate security testing and actions that resemble theft or extortion?
- Communication Protocols: What are the ideal communication methods and expectations when a security researcher discovers a critical vulnerability?
- Vulnerability Handling: How should exchanges and security firms handle vulnerability disclosures to ensure responsible and effective resolutions?
This case underscores the complexities and nuances within the realm of ethical hacking, especially in the high-stakes world of cryptocurrency. While CertiK claims their actions were purely for testing and highlighting security flaws, Kraken initially perceived them as malicious and extortionate. The differing perspectives highlight a potential gap in understanding and communication between exchanges and security researchers.
Key Takeaways from the Kraken-CertiK Saga
Let’s summarize the key points from this developing story:
- Fund Recovery: Kraken has successfully recovered the $3 million in digital assets from CertiK.
- White-Hat Gone Gray? What started as a white-hat hack quickly devolved into accusations of extortion and threats.
- CertiK’s Defense: CertiK claims they were testing security limits and never demanded a bounty, emphasizing no user funds were at risk.
- Industry Debate: The incident has sparked a crucial conversation about ethical hacking, communication, and vulnerability disclosure in crypto.
The Kraken-CertiK incident serves as a potent reminder of the ongoing challenges in cryptocurrency security and the importance of clear communication and ethical guidelines in the cybersecurity space. As the dust settles, the industry will likely be looking at this case to learn valuable lessons and refine protocols for handling future vulnerability disclosures.
Disclaimer: The information provided is not trading advice, Bitcoinworld.co.in holds no liability for any investments made based on the information provided on this page. We strongly recommend independent research and/or consultation with a qualified professional before making any investment decisions.


